Assessing compliance with AWS Audit Manager
Introduction
As in traditional IT infrastructures, firms in regulated industries such as banks or energy providers have strict security requirements to comply with when using public cloud providers as well. However, cloud adoption is often driven by application development teams that are striving for increased speed and agility to launch new features in their application, but don’t care too much about those regulatory requirements. That makes it particularly important for IT governance functions to have effective tools to evaluate compliance with the aforementioned standards and gather evidence that can be provided to their internal or external auditors. Luckily, AWS Audit Manager jumps in to serve that purpose!
In this blog post, we are going to show a basic setup to setup Audit Manager and utilize it to prepare for a security audit based on the CIS benchmark.
Setup
Setting up AWS Audit Manager is fairly simple. Just log into the AWS Console, search for the service, and hit the Launch AWS Audit Manager button.
In the setup dialog, it recommends to enable AWS Security Hub and AWS Config, too. This is because AWS audit manager will utilize these services to perform automated compliance checks. If you haven’t enabled the services before, you should do that right away. There are shortcuts to jump to these services on the bottom of the dialog. Furthermore, enabling AWS CloudTrail is useful, too.
Coming back to the audit manager setup dialog, untick the Customize encryption settings (advanced) checkbox for simplicity, and complete the setup with the button on the bottom of the page.
Creating the assessment
Select Framework Library from the menu. AWS Audit Manager has a number of prebuilt assessment frameworks, which are comprised of controls. Controls can be manual or automated by means of AWS CloudTrail, AWS Security Hub, AWS Config or by periodic execution of AWS API calls.
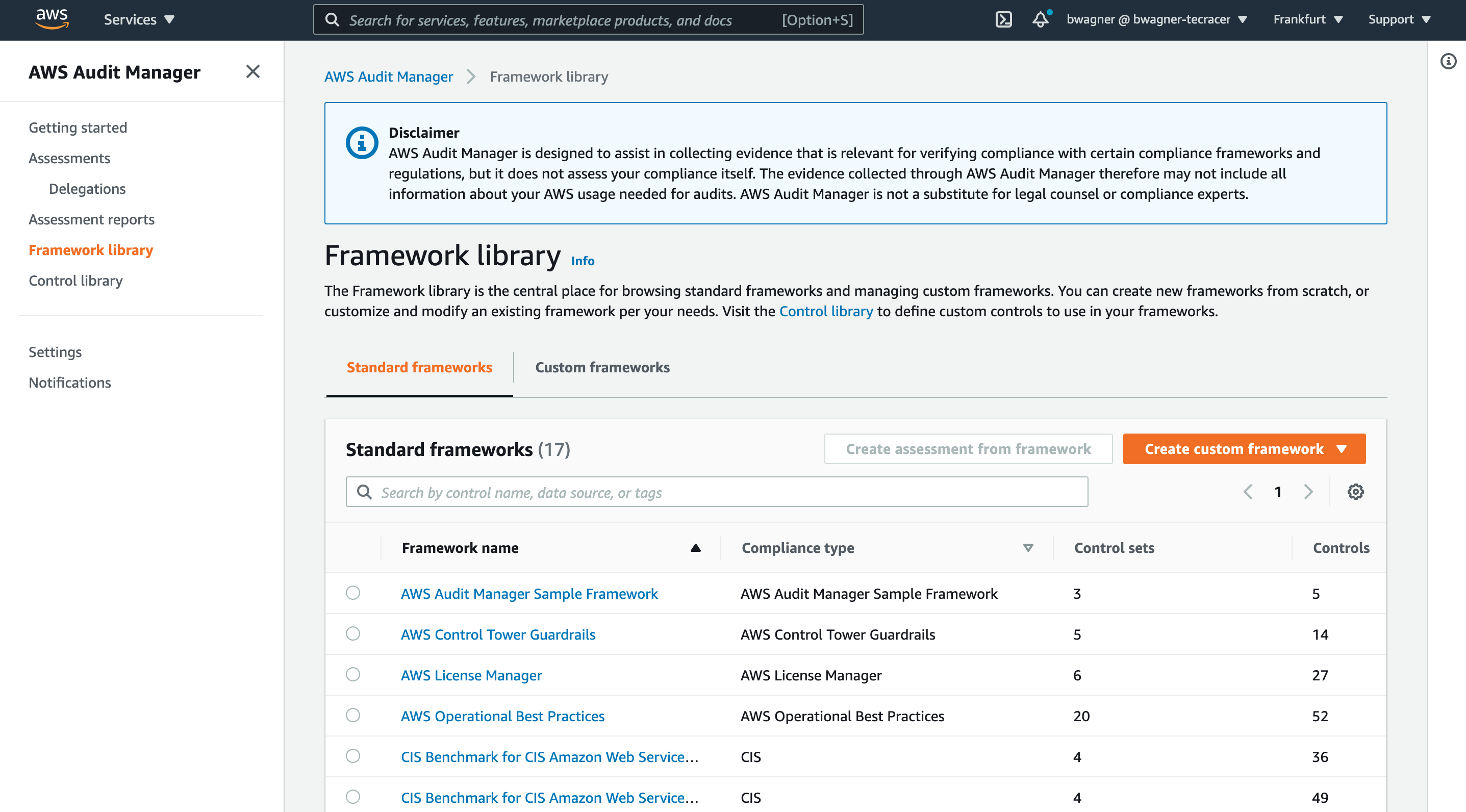
Select the radio button for the CIS Benchmark for CIS Amazon Web Services Foundations Benchmark, v1.3.0, Level 1 and 2 framework. Next, click Create assessment from framework.
On the next page, enter a name for the assessment, e.g. cis-1.3.0-level-1-and-2, a description if you want, and create or select an AWS S3 bucket that will be used to store assessment reports. The CIS framework will already be selected.
Click next, select your AWS account, click next again, and then select all services that shall be in scope of the assessment. In my case, I will select all 154 services, which is a bit burdensome because I need to jump to every single of the 7 pages to select the services.
Click next again, select your IAM user or role as an audit owner (doesn’t really matter for us now), click next once again, and hit the Create assessment button after reviewing the settings that have been made.
Frankly, the UI should simplify the creation of the assessment with some default setting here and there, but fortunately we won’t have to do this too often.
Are we compliant?
Let’s see what we got by now.
Click Assessments in the navigation and select the assessment that we just created. It takes a while to gather evidence so you might wanna pause here and give the service some time to collect some evidence. You should be able to continue after 24 hours at maximum. Eventually, the assessment details page should show how much evidence has been collected so far.
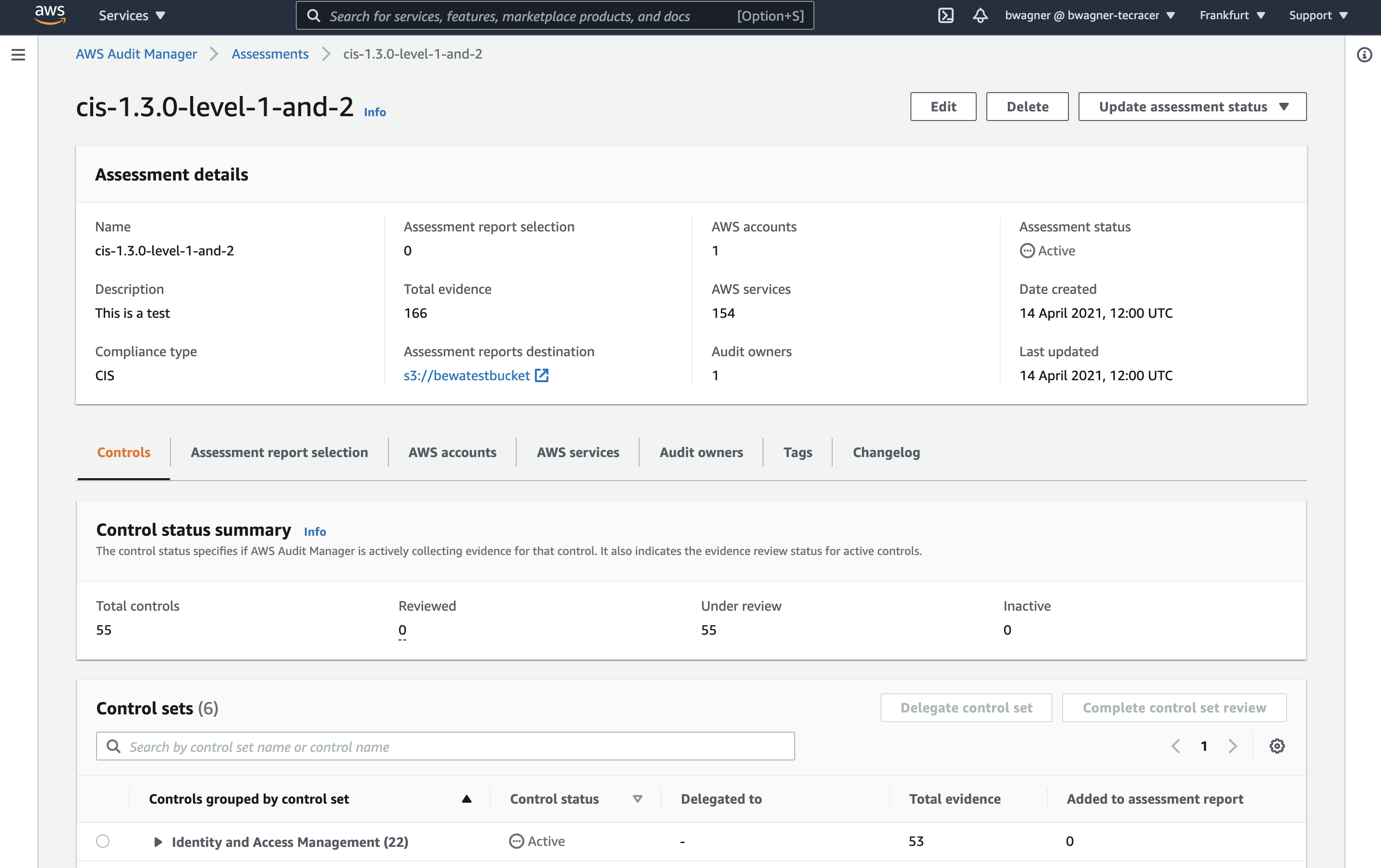
The details page is structured into two sections. The upper panel shows a summary of the assessment configuration and the evidence gathered. Underneath, there are multiple tabs. We won’t go into the details of all of them in this blog post to not puff it up too much. It’s also quite self-explanatory if you are proficient navigating in the AWS console already.
We will stay in the Controls tab which is selected by default. It shows all the controls defined in the regulation or framework; in our case the CIS benchmark. Unfold any of the sections, for example Identity and Access Management, and click on one of the controls.
The controls details page will show you the full original text of the control and an evidence folder per date.
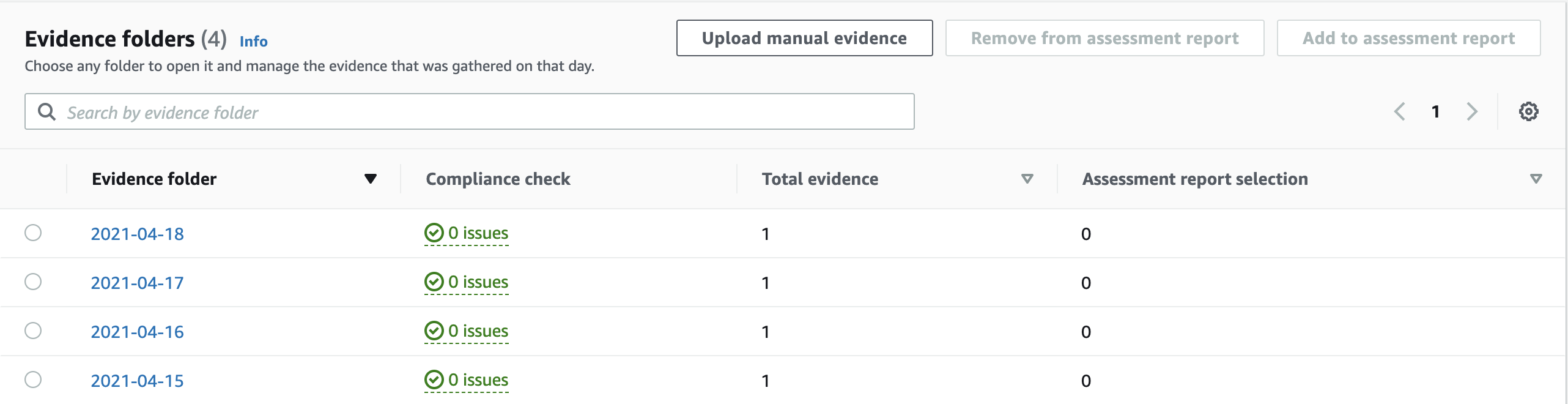
The cool thing here is that the control details page will show you if there are any issues identified from the collected evidence; in other words: If your AWS account is uncompliant with a control, AWS Audit Manager will show you. Honestly, that information should be summarized in the assessment details page as well as it is a bit tedious to check all the controls details pages for potential compliance issues.
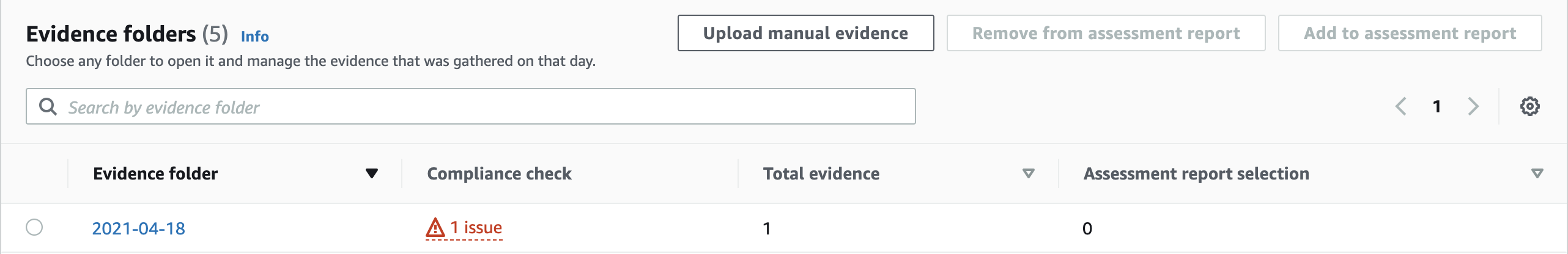
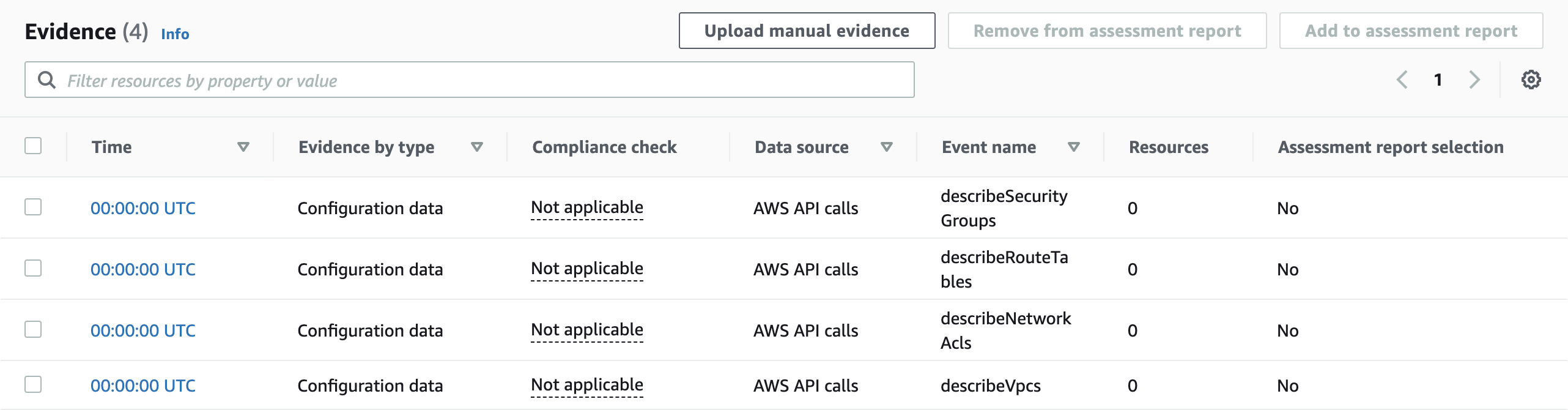
Each evidence folder can contain multiple pieces of evidence, for example for each AWS API call that is used to collect evidence or for different evidence sources which correspond to the data sources explained before (AWS CloudTrail, AWS Security Hub, AWS Config, AWS API calls, as well as manual evidence that can be uploaded into the evidence folder).
A few words on automated report generation
AWS Audit manager even allows you to select individual evidence items and add it to an assessment report which can be downloaded as a ZIP file. The ZIP file will contain a bunch of PDF documents (one for each piece of evidence as well as a summary report (AssessmentReportSummary.pdf). That feature seems very promising, but there’s a lot of room for improvements here. It lacks proper information filtering and the visualization and formatting of these documents seems like it’s still in beta state. Therefore, I did not find that helpful for now but I’ll keep an eye on it as I am certain that AWS is probably already working on ways to make this more user-friendly.
Pricing
All services used for the setup (AWS Audit Manager, AWS Security Hub and AWS Config, AWS CloudTrail) cost money. Thus, better check the pricing details before enabling the services.
Audit Manager and Security Hub offer free trials, CloudTrail has a free tier so you will only be charged for special configurations, and AWS Config is very cheap if you don’t have many resources in your AWS accounts (yet), so trying out the services for a limited amount of time won’t cost you much.
Outlook
AWS Audit Manager tackles a problem that we often see among customers that didn’t invest enough time to set the baseline setup of their AWS cloud usage: Bringing light in the compliance status of the environments.
The service won’t fix the mistakes from the past, but it will create the transparency that is needed to derive an action plan to improve security and compliance, which will typically include identity and access management, networking, encryption, and proper audit logging and thread detection.
Despite some usability issues such as the number of mandatory settings to be made to create an assessment, the lack of a compliance dashboard for an assessment and the poor formatting and information filtering of assessment reports, AWS Audit Manager can be a real problem solver for regulated companies.
Over the last couple of years, we at tecRacer built strong expertise in building fully-blown, enterprise-ready cloud setups that are in line with AWS best practices and common IT security guidelines. We are also an official partner for AWS Well-Architected reviews. So regardless whether you are just looking for someone to take a criticial look at your setup, or if AWS Audit Manager already disclosed some weak spots: We are here to help!
